The rise of email viruses warns email marketers and receivers badly, pushing them to learn the best email security practices. Companies are struggling to ensure secure protocols to do safer business, but still, they may be vulnerable at some point. In addition to all other forms of cybercrime, hackers also target the company’s central computer system to steal or encrypt vital information via malicious email. In the worst cases, the hackers sometimes claim a significant amount to decrypt the data.
According to AAG’s 2025 security report, 91% of cyber attacks occur via phishing email only. Cybercriminals typically use links and attachments in the email body to trick victims into falling for phishing scams. In addition, Astra Security Audit stated that 1 out of every 4,200 emails was a phishing email.
What are email viruses?
Email viruses are malicious codes written by cybercriminals that are sent through emails to the targeted recipients to infect their devices. However, email viruses can spread through links, documents, pictures, and the Calls to Action button (CTA). Cybercriminals hack the email receiver’s devices whenever the victim clicks those elements in phishing emails. Also, there are different types of email viruses. Cybercriminals are designing new malicious codes day-to-day, producing more deadly viruses.
Types of email viruses
There are several types of email viruses, and their categories are as follows: They are as follows:
Direct action virus
Direct action viruses act whenever you click on an infinite element of a phishing email. Cybercriminals use “direct action viruses” to conduct rapid actions. When someone opens a virus-infected email attachment, it quickly spreads to their storage device and infects the files inside it. But it does not contaminate the system files, so this virus can be easily removable from the infected device.
Resident virus
The resident virus is more dangerous than the direct-action virus, as it is swift in action. This virus can attack the file storage and create a copy in the system memory. Therefore, it is also known as the Memory-Resident virus. The resident virus is a bit tough to remove from any device. From memory, the resident viruses can affect any file in the storage (including any virus removal tool).
Boot sector virus
The boot sector virus is another harmful virus that may be included in the email. After installation, this virus works silently and takes effect after the computer’s next boot. Boot sector viruses can only affect computers. It attacks the computer’s master boot record to corrupt the master files. The boot sector virus is hard to remove from the device because the virus can encrypt the entire boot sector. You must clean the whole system and reinstall the operating system (OS) and everything from the ground up to eliminate the virus.
Multipartite virus
A multipartite virus is a combination of the previous three types. Its attacking strategy depends on the computer’s operating system and security software. A multipartite virus can attack the boot sector or the device’s storage files. The virus usually searches for any security holes in the device’s system and attacks that immediately.
Keylogger
Cybercriminals often include keyloggers with an email when they want to track the target for a long time. A keylogger is a spyware virus. When an email receiver clicks a keylogger-infected email link or attachment, it keeps tracking the keyboard. Cybercriminals use this tool to get the victim’s bank information, social account passwords, essential and private emails, user IDs, and their respective passwords.
Macro virus
A macro virus is another deadly email virus. Cybercriminals usually attach macro viruses to email attachments. The macro viruses are written in the macro language. Some popular software programs, such as Microsoft Excel or Word, also use this language. Therefore, this virus targets software rather than computer systems or files. Cybercriminals use Microsoft Excel or Word files with Macro virus code and attach them via email. The virus infects the person’s device immediately whenever a person opens an email containing macro viruses in the form of attached documents.
Spam bot
A spam bot is a particular type of virus. It does not target the victim’s device but attacks the victim’s website or landing page. Although spam bots are not usually distributed through email, cybercriminals implement the spam bots on the target website. A spam bot is generally an automated program that collects valid email addresses from a website. Thus, cybercriminals collect some genuine email addresses through a spam bot and later send some more virus-infected emails to them.
Apart from these common email virus categories, cybercriminals constantly improve their ideas and develop new types of email viruses. Therefore, it’s better to take protective measures against email virus attacks rather than face all of them at once.
Some of the well-known email viruses
To understand the threatening effects of email viruses from history, you should know some of the old email viruses and their worldwide impact. –
Melissa
Melissa is one of the oldest email viruses, released in 1999. It is a macro virus that was distributed as an email attachment. The US FBI (Federal Bureau of Investigation) estimated the cleanup and repair cost of the virus at USD 80 million. They also estimated that more than 300 organizations, including Microsoft Corporation, were affected by this virus.
ILOVEYOU
ILOVEYOU is another widespread virus that took effect in 2000. Hackers shut down several email servers with an email message in the subject line “ILOVEYOU.” A report published on CNN Business stated that the estimated damage caused by the ILOVEYOU virus was 10 million US Dollars. The report also said that this virus infected over ten million computers.
Mydoom (also known as Win32)
In early 2004, Mydoom was spread and sent by email spammers to send junk emails through infected computers. According to NordVPN’s cybersecurity report, the virus affected around 50 million computers globally. And the estimated damage cost was 38 billion US dollars.
WannaCry
WannaCry is a recently well-known virus that was released in 2017. It is one of the dangerous ransomware viruses that spreads through phishing emails. Kaspersky Lab published a report on WannaCry and stated that the virus affected 150 countries, and the estimated damage cost was 4 billion US dollars.
How to recognize email viruses
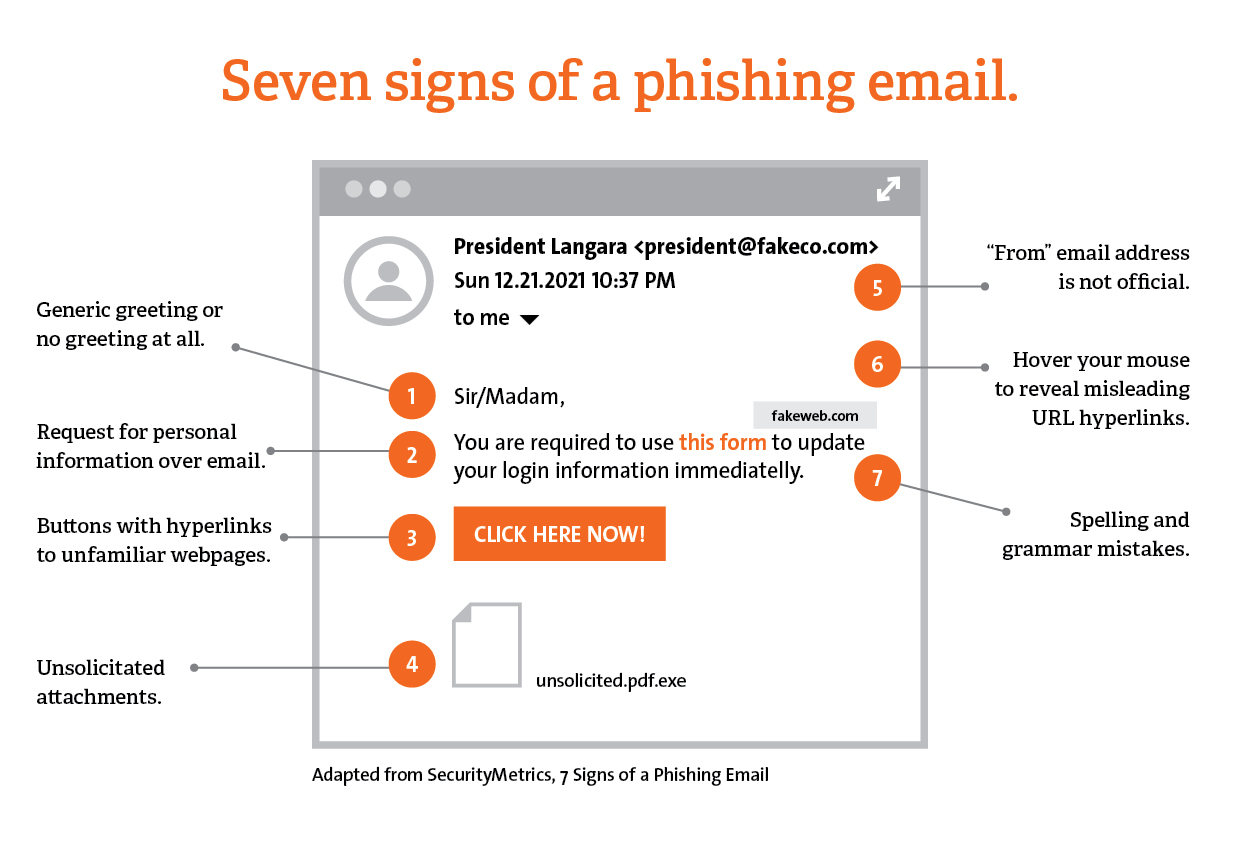
Cybercriminals distribute email viruses through phishing emails. According to EarthWeb’s 2025 research, around 3.4 billion phishing emails are sent daily worldwide. Cybercriminals insert links and attachments into phishing emails, creating a trap for email receivers. But remember that cybercriminals are not professional email marketers. That is why they can make several mistakes while emailing, apart from sending malicious code in the email. For example, let’s look at the image below, where Langara College showed seven signs of phishing emails under their “Be Cyber Smart Program” campaign.
Some more best practices for preventing email viruses
It is undoubtedly scary to deal with email viruses when they enter your system, as getting rid of them might be difficult. However, when cybercriminals encrypt their victims’ data and charge a significant amount to decrypt it, The nightmare for the sufferer then starts.
To lower the risk of email viruses, consider the following recommended practices:
- First and foremost, if you are an email marketer, you must educate your customers about the best email security practices.
- Regarding email marketing, do not buy email lists from third parties. There is a possibility that hackers’ email addresses are on that list.
- Avoid opening any unknown emails. Do not believe even the most alluring subject line of an email. Hackers usually use lucrative and unrealistic email subject lines to attract their victims.
- Even if you open the email by mistake, you are still not affected yet but are very close to being infected by the hacker. So, don’t dare click on any link or attachment at this stage.
- Always be cautious before sharing your email address with anyone. Cross-check the person or brand to determine whether they are legitimate or not before sharing your email address.
- A hacker can still trick you using the email spoofing technique even after ensuring the email sender’s address and brand name. So, be aware of it.
- It is good to use email security software to ensure advanced email security protocols. Such as encrypting email messages, defending against the most recent email viruses and phishing attacks, etc.
- Apart from email security software, you can use free antivirus (such as Microsoft Defender or Avast Antivirus free edition) to protect your device from any downloaded viruses, even from an email.
- Constantly update your browsers, software, and operating systems. Every new patch or update will address security flaws since email viruses can harm more quickly because of outdated software installed in the system.
- You may use an email marketing tool if you are an email marketer. Since the marketing tool uses email authentication standards, the email recipient can realize that it comes from a reliable source.
To summarize
Always remember, you should act smart, not fast! Cybercriminals are far more intelligent than you can imagine. Don’t allow them to infect your computer. You must take as many preventive measures as you can. So, in a nutshell, preventing hackers rather than facing them is always better.












 Contents
Contents
