Beware! Your inbox might be a playground for cybercriminals.
Did you know that according to EarthWeb, 3.4 billion spam emails are sent daily? One of the sneaky tactics they use is called Email Spoofing.
Fear not! This quick guide discusses how to stop email spoofing with all the ins and outs.
Ready to protect your email address? Let’s roll!
Table of Contents
- What is Email Spoofing?
- How to Stop Email Spoofing in Just 4 Steps
- How do Cybercriminals Spoof Emails?
- How do You Know if Your Email is Being Spoofed?
- What Should You Do If Your Email Is Spoofed?
- FAQs on How to Stop Email Spoofing
- Secure Your Email, Secure Your World
What is Email Spoofing?
Email spoofing is a cybercrime. It alters the email header and uses a bogus email address (such as a trusted friend’s name or domain) instead of the genuine one to gain control of your online accounts, spread malware, or steal funds.
Hackers can easily create spoofed emails in the same way spoofed emails can be easily detected. But in some cases, these emails cause colossal damage.
Imagine receiving an email from an address that looks like it’s from Amazon.com, offering a bonus or incentive. Because it seems trustworthy, you click on the provided link.
However, by doing so, you unknowingly give access to cybercriminals who could compromise your account. Always be cautious, even if an email looks legitimate, and double-check before clicking on any links to avoid falling victim to scams.
This is how, every single day, an estimated 3.4 billion spam emails are sent to email users.
How to Stop Email Spoofing in Just 4 Steps
It is impossible to stop receiving spoofed emails in your inbox because of the foundation for sending emails—Simple Mail Transfer Protocol (SMTP). It is a communication mechanism for electronic mail delivery that does not require email authentication.
But you can adopt other countermeasures mechanisms to prevent email spoofing. Just ensure your email service provider allows you to use the required protocols.
Here are 4 simple steps to stop email spoofing—

1. Check Email Headers
Every email service provider has their own way of checking email headers. For Gmail users, to check any suspicious email headers,
- Open the mail and click on the More next to Reply.
- Now click on Show Original.
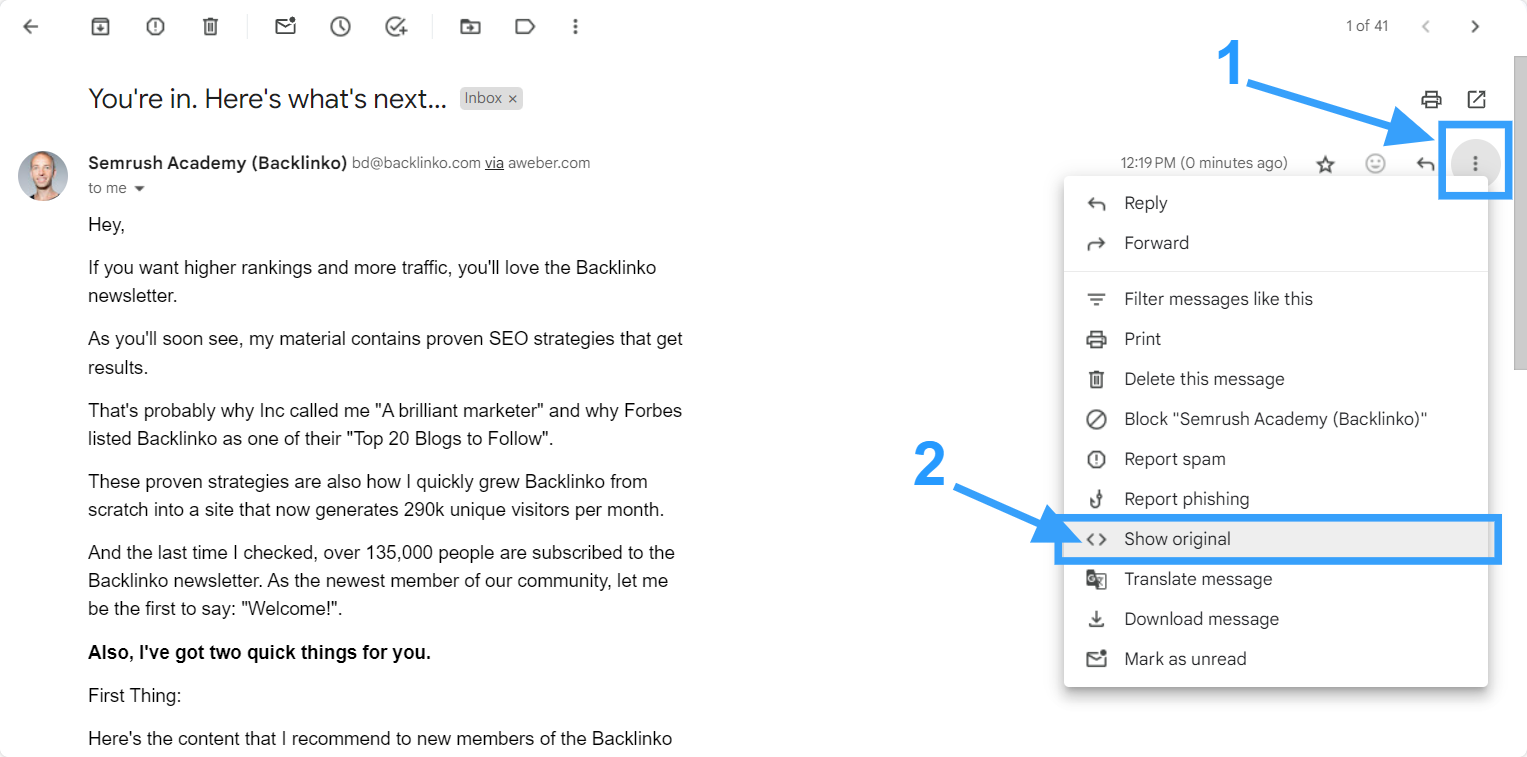
A new window will open with the detail header.
- Now copy the header to the clipboard, paste it on the Google Admin Toolbox Message Header, and click Analyze the Header Above.
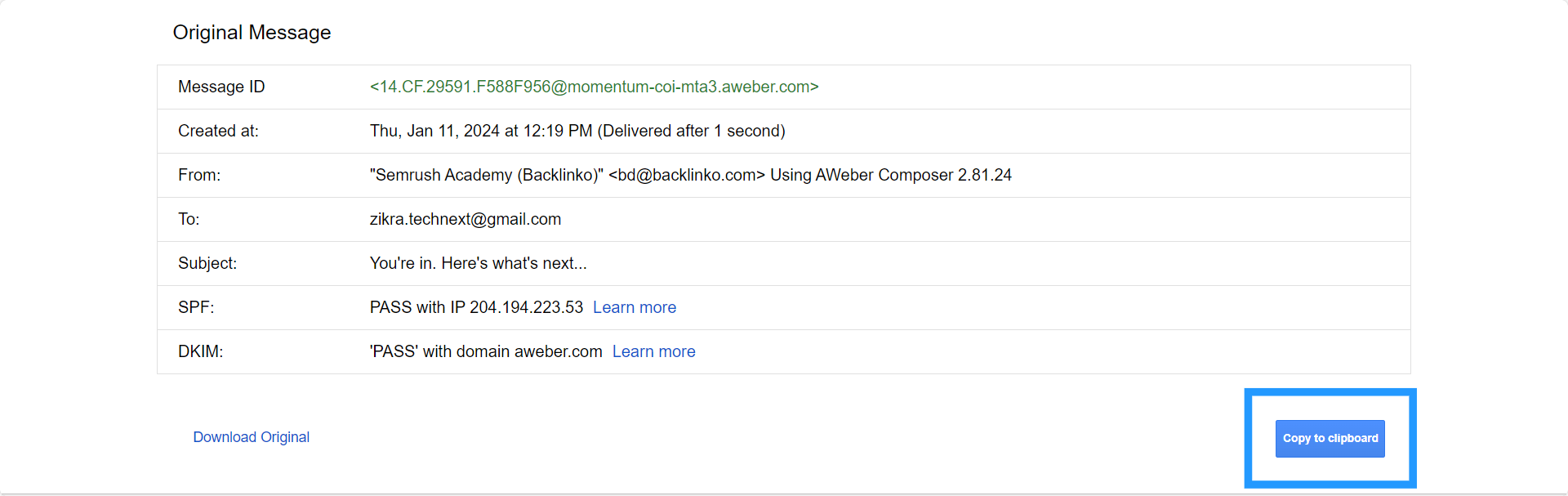
And you will receive the following in detail,
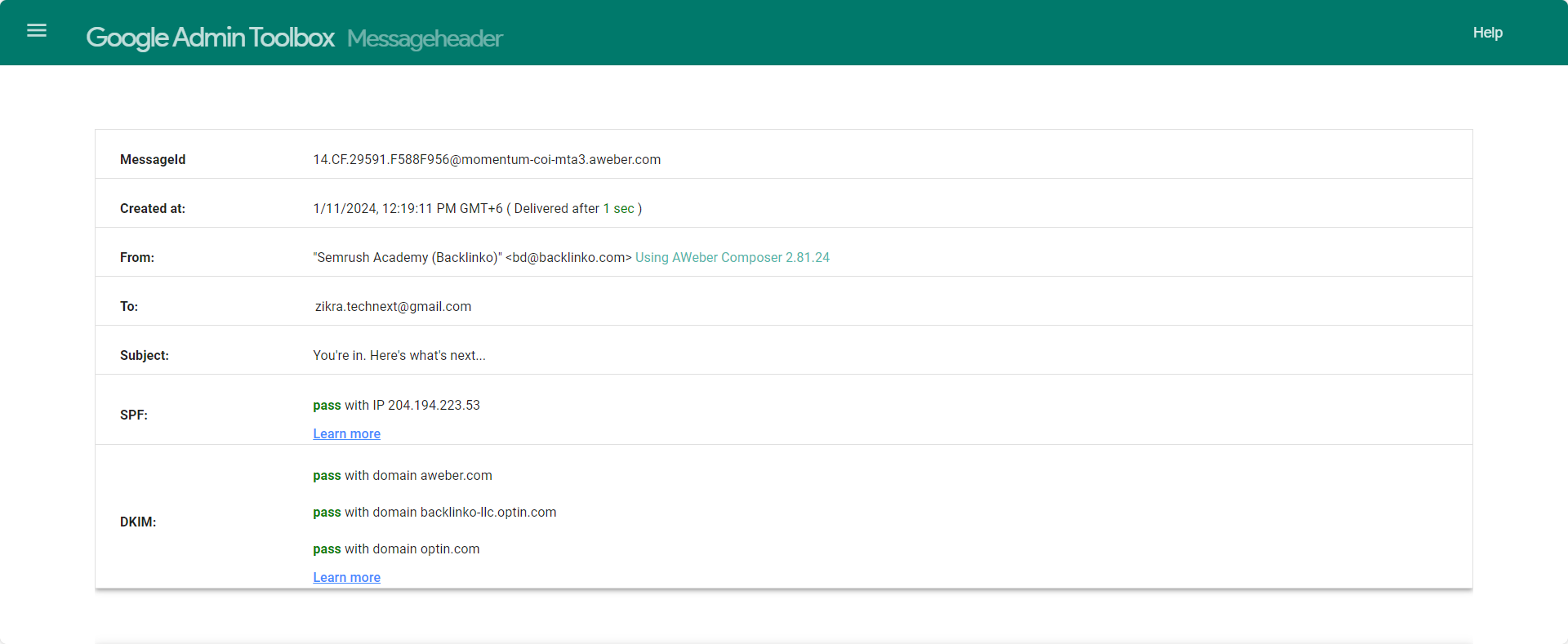
Scroll down and look thoroughly here; you will see some sort of technical stuff—no need to worry about these. Let me make it easier for you. Here, you must look only for the Domain Name and IP Address.
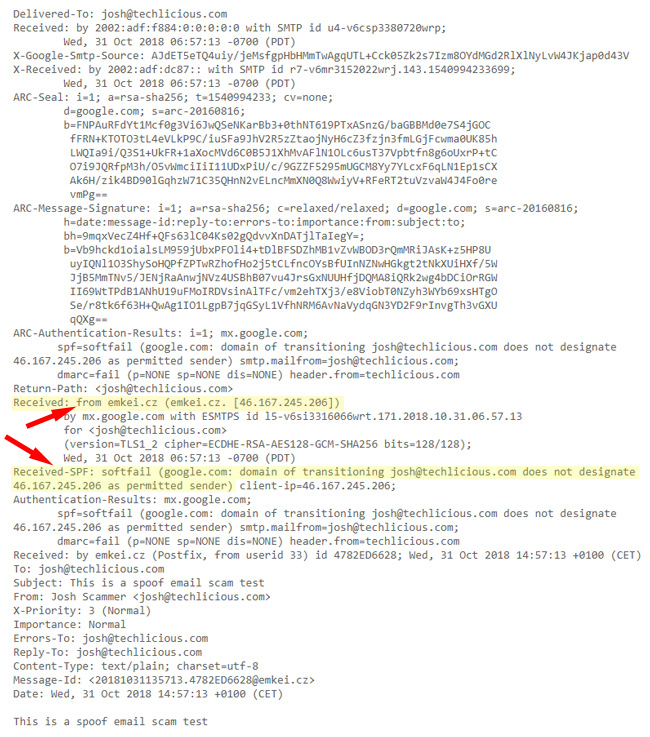
This way, you can check the email header and identify the spoofed emails to stop them.
2. Use Email Authentication Protocols
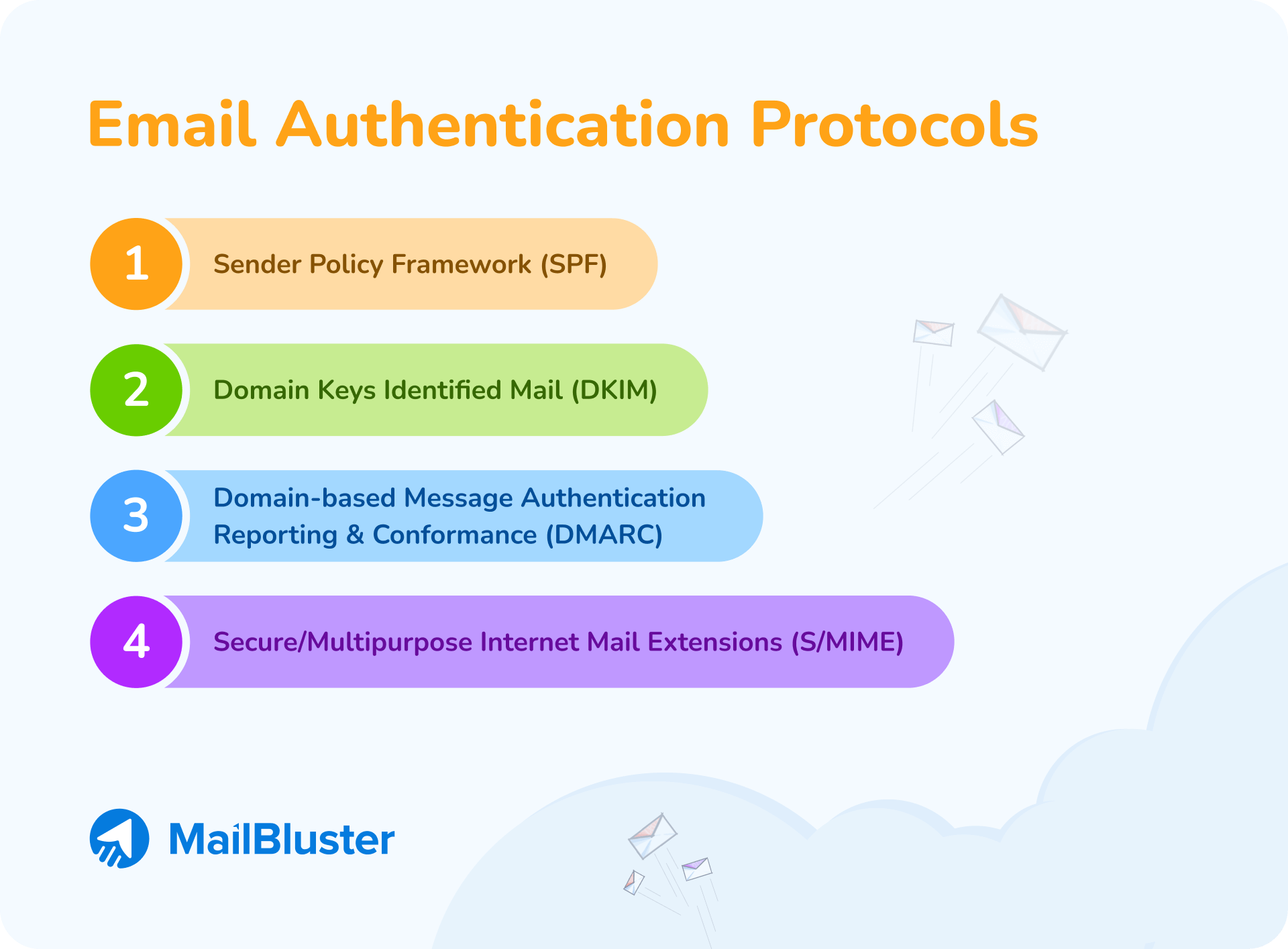
Using email authentication protocols helps to reduce the possibility of using your email address to trap others. You can even stop hackers from spoofing your email.
Email authentication is a technical solution. It helps your email not to be forged. Besides, it verifies where the emails come from and who they claim to be from. It also blocks harmful or fraudulent email uses, such as phishing and spam.
So, make sure your email service provider is providing you with the following email authentication protocols—
- Sender Policy Framework (SPF) – An email authentication protocol ensures the sender is authorized to originate mail from the email sender’s domain.
- Domain Keys Identified Mail (DKIM) – An email authentication protocol notifies the recipient of an email that the domain owner delivered and authorized the message.
- Domain-based Message Authentication Reporting & Conformance (DMARC) – An email authentication protocol developed to allow email domain owners to safeguard their domains from illegal access.
- Secure/Multipurpose Internet Mail Extensions (S/MIME) – An email authentication protocol for sending digitally signed and encrypted messages.
💡 Mailbluster users can set all the protocols to their email through their AWS account.
3. Protect Your Password
Protect your password with intense and complex characters. Also, keep changing your password frequently. It is suggested that the email password be changed every 3 months.
These practices will help you save your email account from cyber criminals. They couldn’t easily get your password and mislead your email address.
4. Keep Your Inbox Organized
While we get a lot of emails every day, it is quite impossible to check all the emails and justify them thoroughly.
So, keep organizing and unsubscribing to unnecessary newsletters. You can avoid getting many emails daily and easily check details simultaneously.
Especially when you run a campaign and send thousands of emails, it is not easy to check every header of email addresses.
In this case, you can use MailBluster to run an effective campaign because it has higher protocol systems to check all the data.
How do Cybercriminals Spoof Emails?
It is very easy to spoof emails in this modern era. Cybercriminals use specialized tools and use or change some data to forge the sender’s email address.
Here are some of the methods that hackers use most often—
- Display Name: Cybercriminals use a tactic called email spoofing through display names. They create fake emails by registering a new email address with a deceptive display name that appears legitimate. As a result, these disguised emails slip into your inbox instead of being flagged as spam.
- Legitimate Domain: Imagine receiving an email from someone claiming to be a customer support specialist, asking for your credentials or other sensitive information in exchange for a fake service.
Would you trust it? Probably!
Here’s how they pull it off: instead of hijacking someone else’s account, they exploit compromised SMTP (Simple Mail Transfer Protocol). SMTP lets them manually set the To and From addresses, giving them the power to deceive anyone.
- Lookalike Domain: Cybercriminals often employ lookalike domains in email spoofing. Since trusted domains are well-protected, attackers create emails with domains that resemble authentic ones, making it difficult to spot the difference.
That is why reading attentively before acting is essential to avoid falling into their traps.
Let’s be careful enough not to get trapped and spoofed by any attackers.
How do You Know if Your Email is Being Spoofed?
When you see abnormal activities in your inbox or irrelevant notifications, assume that your email address has been spoofed.
Most spoofed emails act in the same way. Check the list below to understand if your email account is spoofed or not,
✅ You found a bunch of notifications arise right after logging in to your email saying the message you sent was unable to deliver.
✅ You have received a lot of bounce-back messages from your contact complaining about your spam or unusual emails.
✅ If it is your work email, a DMARC protocol should help you recognize which email to ignore according to the authorization data. Besides, this protocol records the rejected data, which helps to identify next time when they try to spoof you again.
These are the common symptoms of being spoofed by hackers. However, you might experience other dangerous activities like credit card misuse.
What Should You Do If Your Email Is Spoofed?
If you find out your email has been spoofed, you can’t get back to it overnight. You must follow some steps and wait for the recipient’s servers to recognize spam messages.
However, in this duration, follow the steps—
- Keep it private and avoid posting on websites or forums,
- Establish SPF to deter spammers and hackers,
- Change the Password immediately, and
- Contact your email provider.
These initiated activities help you avoid any harm and recover your email address ASAP.
FAQs on How to Stop Email Spoofing
Here are some more quick answers—
1. Where Did Email Spoofing Originate?
Email Spoofing originated with the Morris Worm of 1988.
2. What is the Difference Between Hacked & Spoofed Accounts?
Email hacking and spoofing are not the same thing. They have major differences.
Email spoofing is when someone sends emails with a fake sender address to appear trustworthy. The sender doesn’t have access to your account.
On the other hand, Email hacking means the hacker gains full access to your account, risking your privacy.
Secure Your Email, Secure Your World
Remember, securing your email isn’t just a shield for messages; it’s your superhero cape for the entire online universe.
Stay sharp, keep it secure, and let’s rock that cyber-resilient vibe!












 Contents
Contents
